Attackers have been using OneNote attachments to distribute RAT malware, posing a serious security threat. This malicious activity has raised concerns among cybersecurity experts.
In recent developments, cyber attackers have been exploiting the file-sharing capabilities of Microsoft’s OneNote platform to distribute Remote Access Trojans (RATs) – a type of malware that enables unauthorized access to infected systems. This abuse of a legitimate file-sharing service poses a significant threat to organizations and individuals, as it allows attackers to leverage trusted communication channels for nefarious purposes.
The disguised nature of these attacks makes them particularly insidious, as unsuspecting users may unwittingly download and execute the infected OneNote attachments, leading to potentially devastating consequences. As the cybersecurity landscape continues to evolve, it is imperative for users to remain vigilant and stay informed about emerging threats such as this.
Rat Malware: A Growing Threat
RAT malware, short for Remote Access Trojan, is a concerning cyber threat that is rapidly on the rise. It refers to a type of malicious software that allows attackers to gain unauthorized control over a victim’s computer remotely. The risk it poses is significant, both to individuals and organizations.
RAT malware can be deployed through a variety of means, and one increasingly popular method is through OneNote attachments. Attackers are exploiting the trust associated with this widely used note-taking application to spread their malicious payloads.
The repercussions of falling victim to RAT malware can range from data theft and financial loss to complete system compromise. For individuals, it can result in personal information exposure and invasion of privacy. Organizations face the threat of sensitive data breaches, financial damage, and reputational harm.
It is crucial for individuals and organizations to understand the seriousness of this growing threat and take proactive measures to protect themselves. Implementing strong cybersecurity practices, including keeping software up to date, using robust antivirus software, and educating users about phishing and social engineering tactics, can help mitigate the risk of RAT malware attacks.
Onenote Attachments As A New Attack Vector
Onenote attachments are being increasingly abused by attackers to distribute RAT malware. These attachments are being used as a new attack vector due to their widespread use and trusted nature. Since Onenote is commonly used for note-taking and sharing, attackers are exploiting this method to easily reach more potential victims. By leveraging the trust associated with Onenote and its attachments, attackers can circumvent traditional security measures and increase the likelihood of successful infection. This evasion technique makes it important for users to be cautious when interacting with Onenote attachments, as they can pose serious security risks if not handled carefully.
Methods Of Spreading Rat Malware Through Onenote Attachments
Attackers are using various techniques to spread RAT malware through OneNote attachments. They are employing social engineering tactics to trick users into opening infected attachments. Additionally, attackers are exploiting vulnerabilities within OneNote to distribute malware. They are also concealing malicious files within seemingly harmless attachments, making detection more challenging for users and security systems.
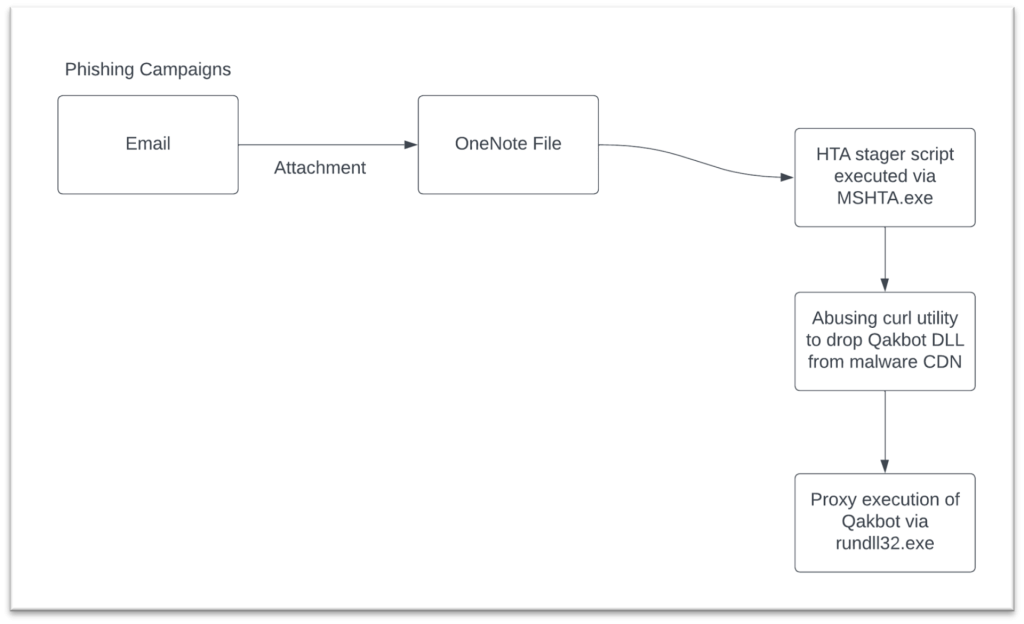
Credit: www.mcafee.com
Real-world Examples Of Onenote Attachment Attacks
In recent times, there have been real-world instances of attackers exploiting Onenote attachments to distribute Remote Access Trojan (RAT) malware. These malware campaigns highlight the evolving tactics employed by cybercriminals to infiltrate systems and compromise sensitive data.
A notable case study involves a targeted attack on a financial institution. The attackers, utilizing malicious Onenote attachments, successfully breached the institution’s defenses, gaining unauthorized access to sensitive customer information and financial data. This incident demonstrates the severity and sophistication of such attacks.
In another large-scale campaign, multiple industries were affected by the malicious use of Onenote attachments. This incident emphasizes the widespread nature of the threat and the need for heightened security measures across various sectors.
It is vital for organizations and individuals alike to remain vigilant and implement robust security measures to protect against Onenote attachment attacks. Regular security awareness training, up-to-date software, and thorough security protocols can help mitigate the risks associated with this emerging threat.
Mitigating The Threat And Protecting Against Onenote Attachment Attacks
Attackers have been increasingly utilizing Onenote attachments to distribute RAT (Remote Access Trojan) malware, posing a significant threat to individuals and organizations. To safeguard against such attacks, it is crucial to implement effective security measures and follow best practices.
For individuals:
- Exercise caution when opening or downloading Onenote attachments from unknown or suspicious sources.
- Keep your antivirus software up to date and regularly scan your system for any potential threats.
- Avoid clicking on suspicious links or email attachments, even if they appear to come from trustworthy sources.
- Enable automatic updates for your software and operating system to ensure you have the latest security patches.
- Regularly backup your important files, either on an external device or through cloud services, to mitigate the impact of potential malware attacks.
For organizations:
- Ensure the implementation of robust security policies and procedures, including proper user access controls and strong password management.
- Regularly train employees on recognizing and avoiding potential phishing attempts or suspicious email attachments.
- Deploy advanced threat protection solutions to detect and block malicious activities.
- Conduct regular security audits to identify and address any potential vulnerabilities in your systems.
- Collaborate with security experts and stay informed about the latest trends and techniques used by attackers.
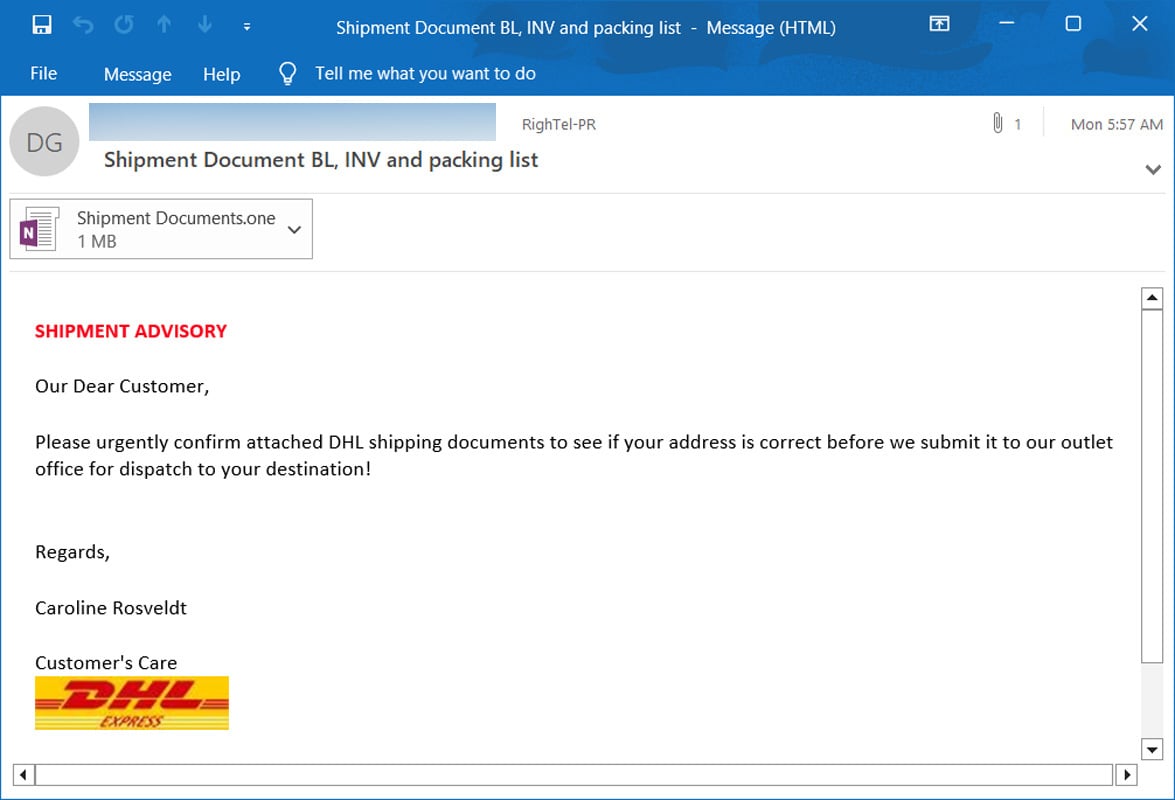
Credit: www.bleepingcomputer.com

Credit: securityaffairs.com
Frequently Asked Questions On Attackers Abusing Onenote Attachments To Spread Rat Malware
How Are Attackers Abusing Onenote Attachments To Spread Rat Malware?
Attackers are taking advantage of the popular note-taking application, OneNote, by embedding Remote Access Trojan (RAT) malware within its attachments. These attachments, which often come in the form of harmless-looking files, serve as a covert means for attackers to gain unauthorized access and control over targeted systems.
Why Are Attackers Choosing Onenote Attachments As A Method For Spreading Malware?
OneNote attachments are an attractive choice for attackers due to their widespread use and the trust users place in the application. By disguising malicious code as innocent files within OneNote, attackers can easily deceive users into opening these attachments, allowing them to exploit vulnerabilities and execute their malicious intentions undetected.
What Risks Are Associated With Rat Malware Spread Via Onenote Attachments?
RAT malware distributed through OneNote attachments poses significant risks to individuals and organizations. Attackers can exploit the compromised systems to exfiltrate sensitive information, monitor activities, execute unauthorized commands, and even launch secondary attacks. These risks make it essential for users to remain vigilant and implement robust security measures to protect against such threats.
How Can Users Protect Themselves From Rat Malware Spread Via Onenote Attachments?
To safeguard against RAT malware spread through OneNote attachments, users should exercise caution when opening any attachments, even if they appear to come from trusted sources. It is crucial to keep security software up to date, regularly back up important files, and practice safe browsing habits.
Additionally, educating oneself about common phishing techniques and employing strong and unique passwords can significantly enhance protection against such attacks.
Conclusion
Onenote attachments have become a new target for attackers to distribute RAT malware. This concerning trend highlights the importance of staying vigilant and implementing strong security measures. Users should be cautious when opening or downloading any attachments and ensure their devices are equipped with up-to-date anti-malware software.
By staying informed and taking proactive steps, we can better protect ourselves from falling victim to these malicious attacks. Stay safe online!
